We collect and publish covertly filmed video footage in accordance with all applicable laws.
Key findings
- Ava Labs connected their Avalanche blockchain to other blockchains using the centralized Avalanche Bridge.
- Using advanced blockchain transaction tracing, shared in a format that makes verification easy, we prove beyond reasonable doubt that the bridge is used to launder tainted crypto assets on a massive scale.
- We trace almost $300M of tainted crypto being deposited into the bridge, mainly by North Korean hackers, who help the rogue state circumvent sanctions that reduce the funding available for its illegal nuclear weapons program.
- Retail users of the bridge may now receive tainted assets from the bridge in exchange for their legitimate assets.
- Emin Gün Sirer and/or Ava Labs should urgently make a statement and engage organizations that can deal with the tainted assets that are in their possession.
- Ava Labs should shutdown the bridge until technical flaws that allow it to be used as a mixer are addressed.
Corruption of Retail Assets
Ava Labs is the for-profit company that develops, promotes and operates the Avalanche blockchain. The company also operates the "Avalanche Bridge." This service allows users to deposit assets they hold on other blockchains, and receive wrapped versions of the assets on Avalanche, where they can be used in DeFi systems installed there, such as borrowing and lending services. At a later date, users can redeem the wrapped assets for the underlying assets, which Ava Labs maintains in a pool. The assets desposited by users include bitcoin, and assets on Ethereum, including ether, Daicoin and Tether.
The Avalanche Bridge has retail users firmly in mind and has been widely promoted by Ava Labs. However, for reasons we shall explore, bad actors including North Korean hackers and Russian spies, have deposited almost $300M in tainted and stolen assets into the Avalanche Bridge. Oftentimes the assets have been transferred from dark net markets, mixers, or accounts that are banned by OFAC (Office of Foreign Assets Control). These assets have become co-mingled with bonafide user assets in the pool of assets that Ava Labs maintains.
Retail users could now be subjected to financial loss:
- Desposited assets swapped for tainted.
When a retail user redeems their wrapped assets,
instead of receiving the bonafide assets they originally deposited into the pool, they may receive
tainted or stolen assets, which cannot be sold on centralized exchanges, or should be returned
to their rightful owner;
- Acquired assets tainted.
A retail user who legally acquired wrapped assets using the DeFi systems on Avalanche, may have
the same problem on redemption, and;
- Risk of seizure. Authorities may now seize the entire pool of assets that Ava Labs maintains for the Avalanche Bridge, now that the nature of its contents have been exposed.
North Korea and Illegal Nuclear Weapons
Funding illegal nuclear weapons programs.
North Korea is a rogue state with an illegal nuclear weapons program, which threatens many countries, including America. Because international sanctions against North Korea deny them access to funds, they seek illicit sources of funds. Among these, Lazarus, a hacker group linked to the North Korean regime, steals cryptocurrency, and then launders it through various means. It appears that the Avalanche Bridge has become a key means for them to swap stolen assets for clean assets, which are more easily laundered.
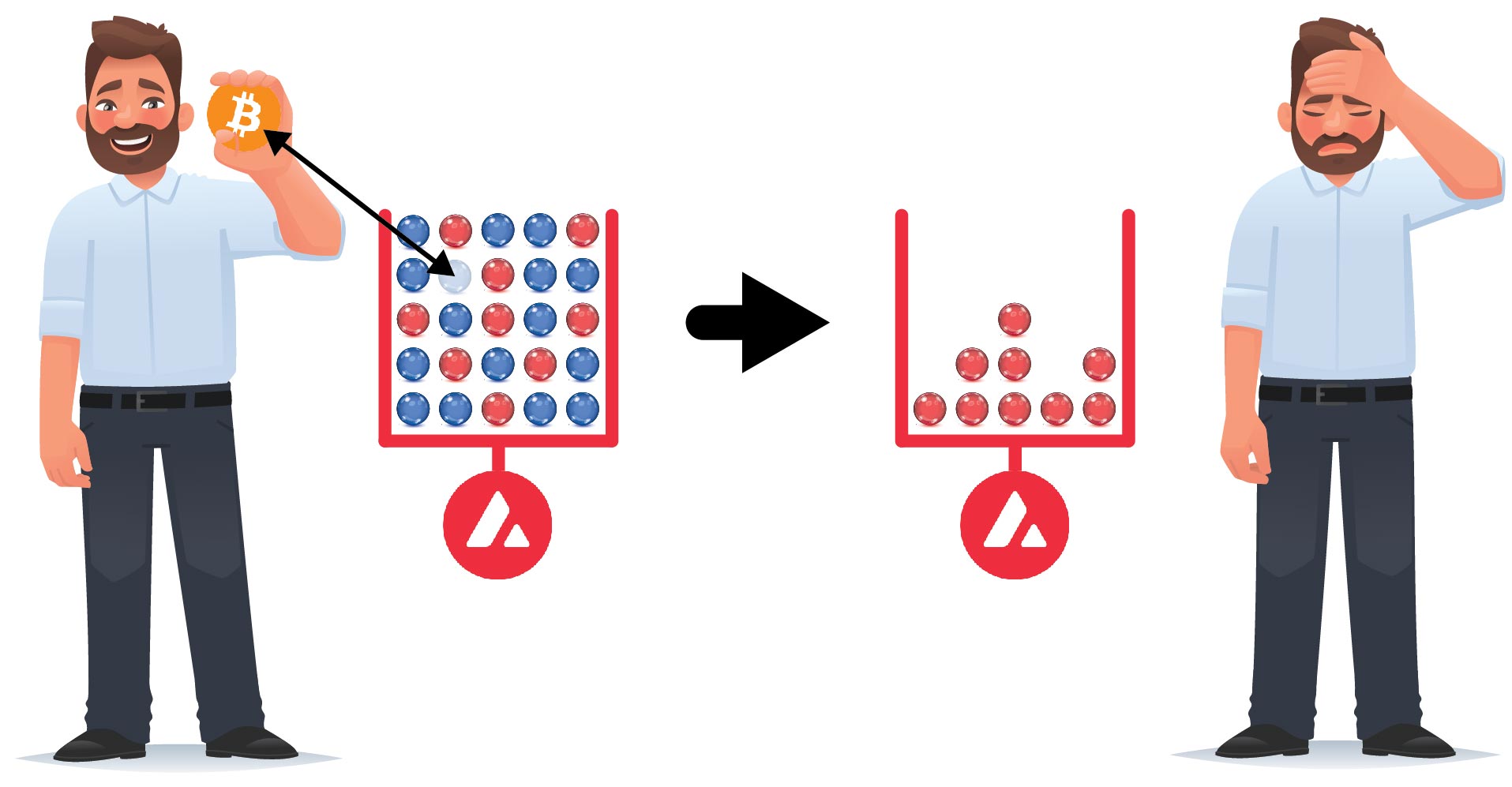
Blue Marble. Red Marble.
Using the Bitcoin network, it is possible to trace individual batches of coins, such that a batch can be determined to be stolen, originate from an account sanctioned by OFAC, a dark net market, or has been passed through a mixer. Other cryptocurrencies, such as ether, can be collected into a single balance at an address and indistinguishably mingled. However, if an address is controlled by a centralized entity such as Ava Labs, an authority may still determine some portion are stolen, or belong to nefarious entities, and lay claim to them.
The pool of assets that Ava Labs maintains for the Avalanche Bridge, which back the wrapped assets, can therefore be thought of like a bag of marbles, where bonafide balances of assets are blue marbles, and tainted or stolen assets are red marbles. To avoid loss, a retail user must redeem their wrapped assets for blue marbles, and do so while the bridge remains free to operate.
If a wrapped asset balance is redeemed for a red marble, such as a stolen balance of bitcoin, in principle the red marble can be re-deposited into the Avalanche Bridge, and then redeemed again, for another chance at getting a blue marble from the bag. This process can be repeated until a blue marble is obtained. However, over time, the use of such tactics will increase the concentration of red marbles in the bag, making it harder and harder for users to obtain blue marbles. In the end, only red marbles will remain.
How Did This Happen?
Ava Labs built the Avalanche Bridge in a centralized way, and neglected to add systems that properly checked the source of assets being deposited. (Ava Labs is a corporation we have covered before in Case #3 and Case #5.)
To capitalize on the crypto bull run, the corporation had quickly adapted the open source software that powers the Ethereum network, to create Avalanche, a completely new Proof-of-Stake network, which now primarily runs on cloud services such as Amazon Web Services. Their next step was to import clones of the DeFi systems running on Ethereum by promising to pay $180M to its developers. However, for these cloned DeFi systems to be useful, they also needed access to the assets stored on Ethereum. To solve this problem, Ava Labs built and operated the Avalanche Bridge.
As explained and exposed by spy video in Case #5, the Avalanche Bridge depends on centralized trust in Ava Labs. Rather than developing a provably secure public network protocol, Ava Labs chose to take a shortcut, and build using SGX "security hardware." This runs secret code developed by Ava Labs, which creates the Avalanche Bridge. However, because it runs inside a private "enclave" to obscure its workings, hackers likely calculated that this would also obscure asset movements, making it the perfect crypto mixer/tumbler for use in their money laundering efforts.
Blockchain Tracing Data
The scale and nature of the problem can be understood using advanced blockchain tracing. In one of the most successful examples of blockchain analysis ever performed, we trace the movement of stolen and tainted assets into the Avalanche Bridge.
The document we share allows you to click on the transactions shown to automatically open them inside an independent blockchain explorer, making it easy for anyone to verify the asset flows.
Our research tracks crypto assets being deposited into the Avalanche Bridge from seven types of sources: mixers, OFAC sanctioned addresses, dark net markets, high risk exchanges, illicit actors, scammers, and stolen funds.
Download the blockchain analysis: c6-avalanche-bridge-disaster.pdf
Proposed Solution
By promoting the sale of AVAX tokens to retail investors, Ava Labs corporation, and its founders and investors, have accumulated huge wealth — while those same retail investors have often found themselves holding bags of tokens heavily in loss. It is time for Ava Labs both to backstop their community and prevent further funds being laundered for Lazarus and others. They should immediately freeze the pool of assets backing the Avalanche Bridge, and provide them to the relevant authorities. Then, they should create a new "compensation service," which allows those holding wrapped assets to redeem them for assets that are not stolen or tainted, which Ava Labs can purchase from exchanges such as Coinbase or Binance.
Taking these steps will protect their users from loss, and also prevent stolen and tainted assets from being withdrawn and re-distributed throughout the crypto ecosystem. If such actions are not taken quickly, experienced crypto users may extract all untainted crypto assets from the Avalance Bridge, ensuring that the retail investors whom Ava Labs induced to deposit clean assets, may have to withdraw tainted tokens (as explained in "Blue Marble. Red Marble"). This questions is: will Ava Labs do the right thing to protect those it induced to use the Avalanche Bridge, and prevent further money laundering via its centralized systems?
Read more case investigations...
We show the public what goes on behind the scenes in crypto. If you can help, please become a whistleblower.